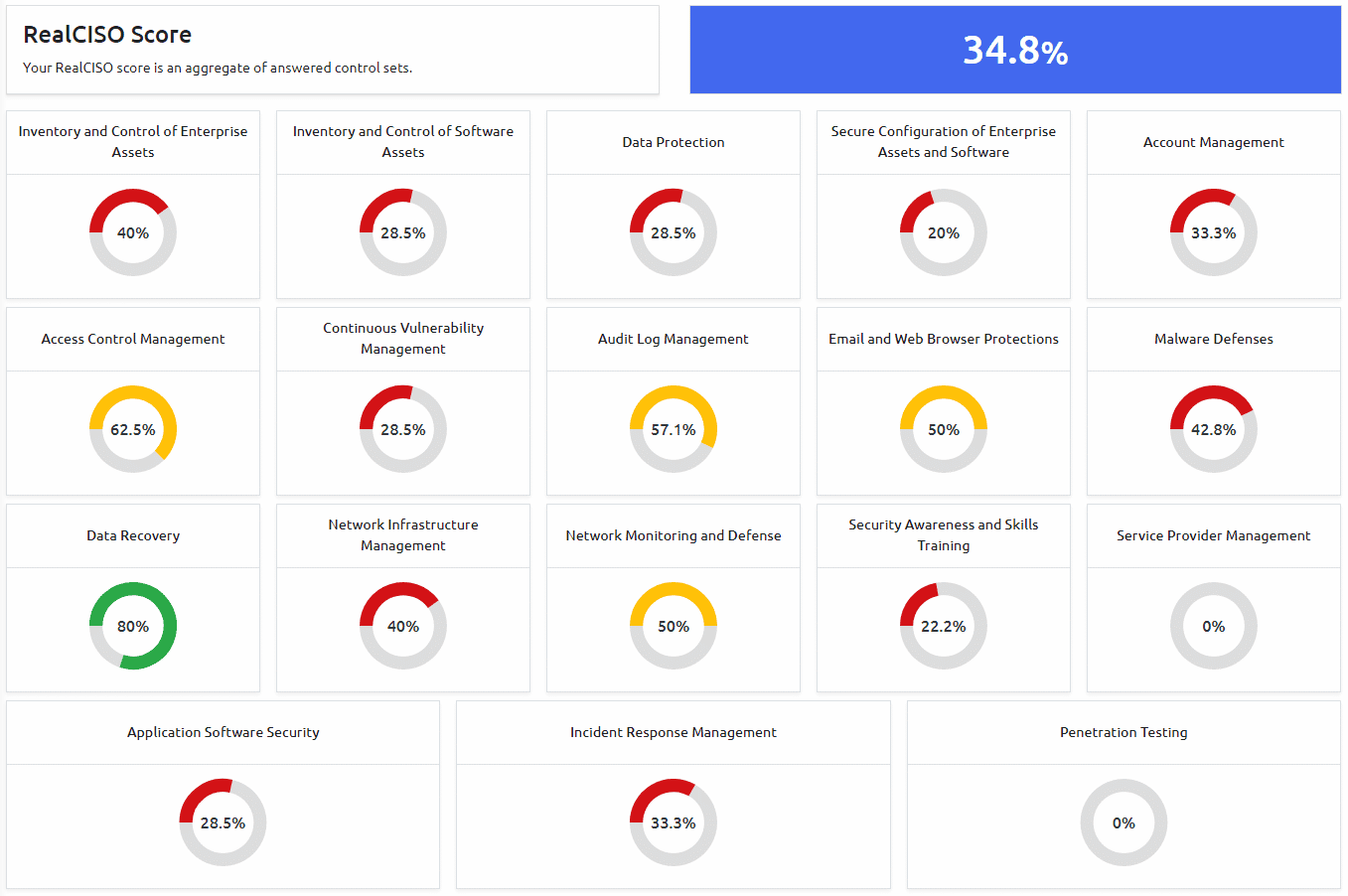
Best Cyber Risk Dashboard Features
A cybersecurity dashboard should provide a comprehensive overview of an organization’s cybersecurity posture, making it easy for board members and leaders to understand and quickly identify any potential risks or vulnerabilities.
Key Features
Here are some key features to consider:
- Real-time monitoring: The dashboard should continuously monitor the organization’s networks, systems, and devices for any security threats or anomalies. This allows the board to stay informed of any potential issues as they arise, rather than having to wait for regular reports.
- Threat intelligence: The dashboard should provide real-time updates on the latest cyber threats and vulnerabilities, including information on new malware, phishing attacks, and other types of cybercrime. This can help the board understand the current threat landscape and make informed decisions about how to protect the organization.
- Risk assessment: The dashboard should include a risk assessment module that provides a comprehensive view of the organization’s overall risk profile. This could include information on the likelihood of a security breach, the potential impact of a breach, and any vulnerabilities that need to be addressed.
- Compliance tracking: Many organizations are subject to various cybersecurity regulations and standards, such as PCI DSS or HIPAA. A high level cybersecurity dashboard should include tools for tracking compliance with these regulations, including alerts for any potential non-compliances.
- Asset management: The dashboard should provide an inventory of the organization’s assets, including information on the type, location, and security status of each asset. This can help the board understand the organization’s overall cybersecurity posture and identify any areas that need additional protection.
- Incident response: In the event of a security incident, the dashboard should provide tools for managing and responding to the incident. This could include a timeline of events, details on the nature of the incident, and recommended actions for addressing the issue.
- Customization: The dashboard should be customizable to meet the specific needs and priorities of the organization. This could include the ability to create custom reports and alerts, as well as the ability to tailor the dashboard to different roles and responsibilities within the organization.
Conclusion
Overall, a high level cybersecurity dashboard should provide the board and leaders with a clear and concise overview of the organization’s cybersecurity posture, as well as the tools and information they need to make informed decisions about how to protect the organization from cyber threats.
See how RealCISO can help you today.
