Choosing a vCISO platform isn’t about automation.
It’s about running a security program.
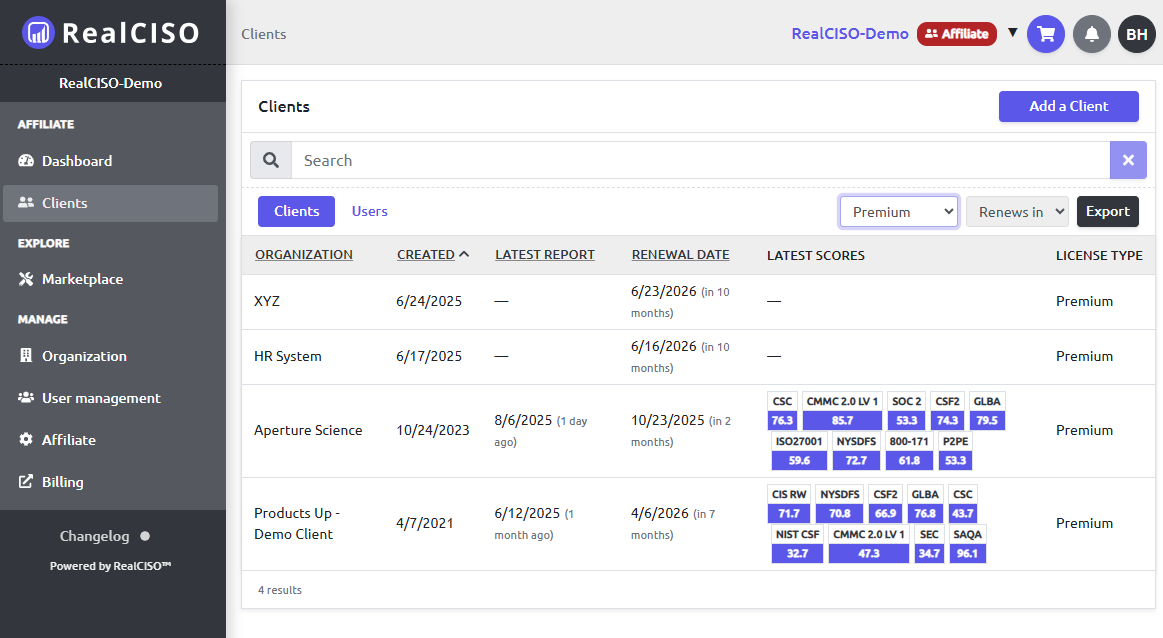
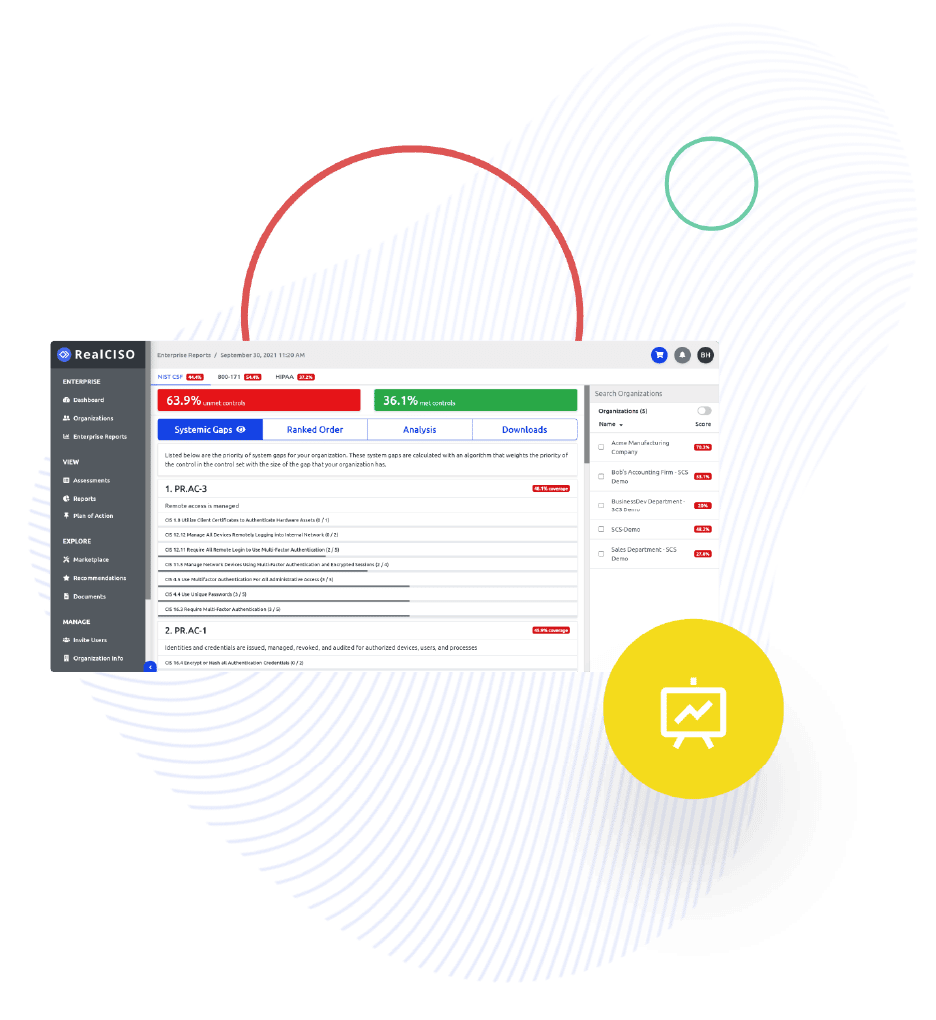
Both RealCISO and Cynomi help service providers deliver cybersecurity services.
But they solve different problems — and that difference determines whether your clients actually operate security or just receive recommendations.